Editor’s Note: The author of this article works full-time in law enforcement in a major metropolitan area of the United States, within a state that has used StingRay devices and other cell phone surveillance systems for various investigations. Due to the sensitive nature of this topic, his article has been published under a pseudonym.
It’s safe to assume our readers fall into one of two groups: you know your cell phone tracks you constantly without your permission, or you’re unaware of the potentially serious privacy risks from the neat little device in your pocket. Being in the latter category doesn’t make you wrong — most people tend not to think about things that haven’t affected their lives yet, or dwell on dangers they believe are outside their control. However, when you’re in a particular line of work, the thoughts and ideas mentioned above constantly run through your mind. As writers in this industry, we often joke about being on government watch lists, but those jokes lose their humor when Big Brother may actually be watching.
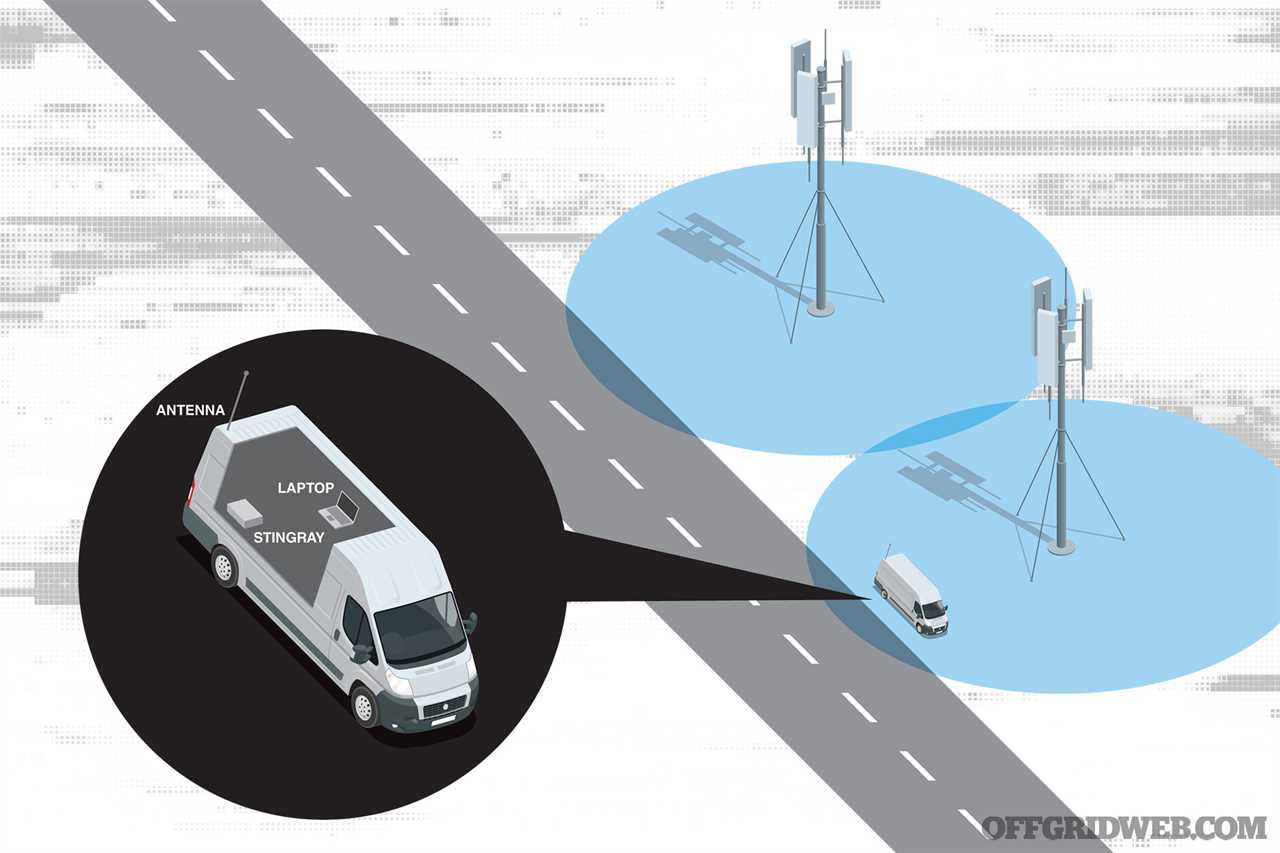
Above: Cell phones automatically connect to nearby towers, but a StingRay device can drown out these towers within a targeted radius, tricking devices into connecting to it instead. The StingRay then collects data and passes it along to the real tower.
If you’ve been watching cases of domestic surveillance in the United States over the last 20 years, you may have heard references to a surveillance device known as a StingRay. So, what is the StingRay, you might ask? Well, it’s not the animal that killed Steve Irwin. It’s a whole different animal in terms of what it can do. Keep in mind that some of this information can get pretty technical, so I’ll do my best to make this as easily readable as possible.
According to a report by the American Civil Liberties Union (ACLU), there are at least 75 agencies in 27 states that are currently known to use StingRay surveillance devices — the actual count is believed to be much higher, since “many agencies continue to shroud their purchase and use of StingRays in secrecy.” On a federal level, users include all branches of the military as well as the FBI, NSA, DEA, ICE, ATF, and even the IRS. However, the devices are also employed by numerous state and local police departments.

Above: The transition from a legitimate cell tower to a cell site simulator is seamless, and the typical user will have no idea that anything unusual has occurred.
Terminology
Before I get started, let’s go over two acronyms I’ll be using. These are important for you to know in general as they are things that can link you to a device:
IMSI: International Mobile Subscriber Identity is a 14- to 15-digit number that identifies your specific device on a cellular network
IMEI: International Mobile Equipment Identity is a 15-digit number that identifies a device but does not have a permanent tie to the owner(s)
For further phone identifier information, go to imei.info/FAQ-what-is-IMEI
How Does the Stingray Work?
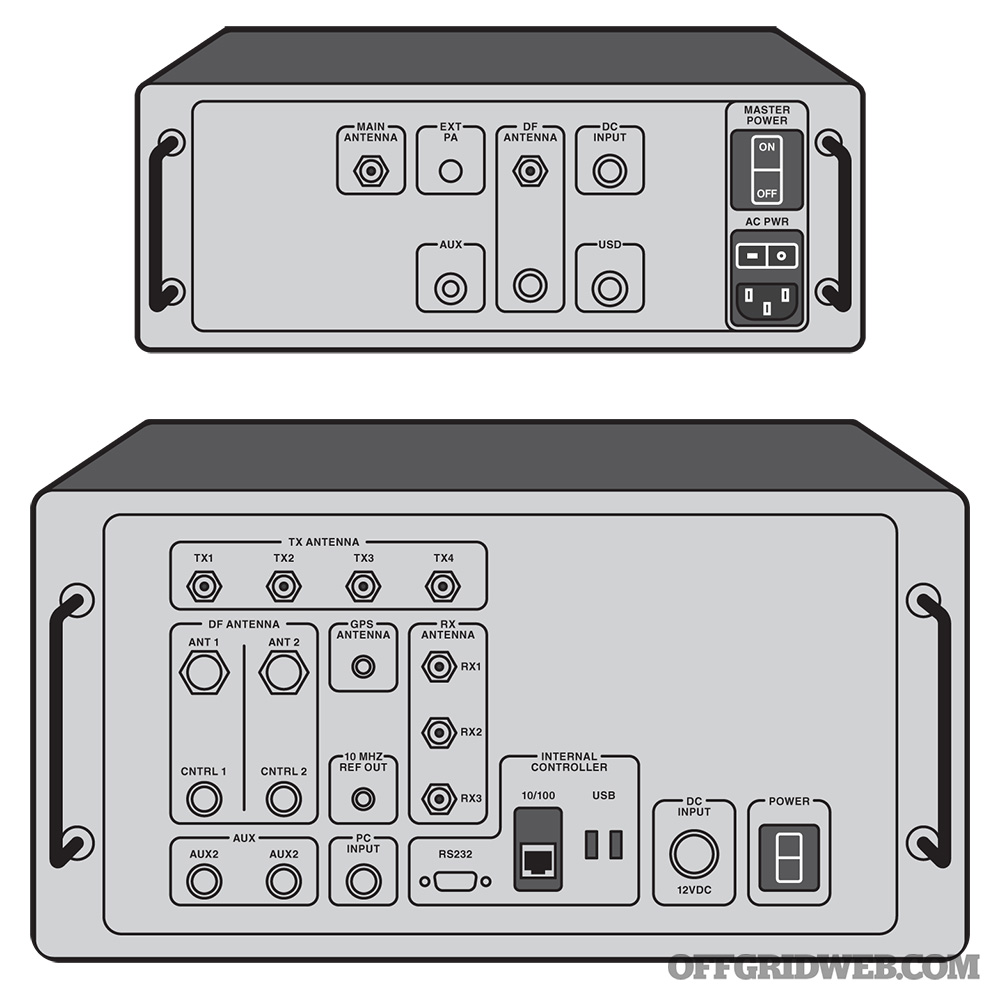
Above: Few images of these devices have been released to the public. These illustrations show the layout of two known variants, the StingRay and StingRay II. A document obtained by VICE magazine showed a StingRay II package was offered to Rochester Police Department in New York for $148,000.
The StingRay is a suitcase-sized device created by L3Harris Technologies, formerly known as the Harris Corporation. It allows the user(s) to gather information about a device, and as a result, a person by multiple methods. The StingRay is designed to be used while mobile or stationary; the live use of the device is conducted by a secondary operator via computer. Due to advancements in technology, the ability to hide the device and antennae have significantly improved in recent years, leaving the public utterly unaware of a StingRay’s location.
The primary application we’ll be going over is using the StingRay as a cell site simulator. A cell site simulator is just what it sounds like — the device impersonates a cell tower. The difference is the simulator will put out a more robust signal that essentially forces smartphones, tablets, and other cellular devices in the area to connect to it. Once your device connects to the StingRay, the IMSI, IMEI, GPS location, and much more information about the device is collected. The connection also stops a device from connecting to an actual cell tower, so certain functions of the device can be disabled on demand. The StingRay can intercept calls, text, and other data depending on the model.
Keep in mind that authorities can still obtain all of this information through traditional investigative channels, by contacting a cellular service provider and requesting data with a warrant. The StingRay is an alternative tool that can be exploited and manipulated to gather information on large groups of subjects without their knowledge, and as we’ve seen from past examples, without a warrant.
Real-World Cell Phone Surveillance Cases

Above: The Los Angeles Police Department was involved in a 2013 scandal that indicated StingRay devices had been used extensively for investigations without warrants and were intercepting private data from innocent bystanders.
Starting with a warrantless use case, let me first address one thing: There are multiple exceptions that allow warrantless searches, granted by the supreme court; there are also ways to get an exigent data request without a warrant. Authorities are still required to get a search warrant within a reasonable amount of time for the collected information or data. An example of an exigent request could be live location data from a cell phone provider for a kidnapping suspect. When going over these cases, let’s look at the facts of the case — I want you to think of how devices such as the StingRay could be abused in certain situations.
The first case, 15-CF-322, originates from the Metropolitan Police Department in Washington, D.C. The case facts are explicit, so I will do my best to make them easy to read. A male, Jones, met a woman for a paid sexual encounter. During that encounter, he forced her to perform sexual acts at knifepoint, then robbed the female and another female who came with her of their belongings, including cellphones. A police report was made, and the StingRay device was used to track Jones’ and a victim’s phones without a warrant. Jones was arrested and subsequently found guilty of the crimes. However, he fought the conviction to the court of appeals, where the following ruling was made in September 2017: using a StingRay type device violates the Fourth Amendment (unreasonable searches and seizures) and a warrant must be authored when utilizing the StingRay. The court then ruled to reverse the conviction unless the arresting agency could prove the use of the StingRay on Jones’ device did not contribute to the verdict. This was the case that paved the way for true rights when it comes to our cellular data privacy. It also showed a local law enforcement agency’s willingness to abuse million-dollar technology in order to spy on citizens.

Above: Washington, D.C., has been the epicenter of more than one controversy regarding use of StingRay devices, both by local law enforcement and by unknown, potentially foreign entities.
Another case comes from the Los Angeles Police Department (LAPD) in 2013. The LAPD has used the StingRay device since approximately 2006; in 2013, information about how often it was being used was revealed to the public. The LAPD used the device to assist in locating burglars, drug dealers, and murderers. LA Weekly reported that LAPD had 155 cellular phone investigations within four months, but only requested 21 search warrants during that time. In many of these cases, the privacy of citizens was blatantly disregarded. Private data including device information, text messages, or other data transmissions were able to be intercepted by the LAPD from individuals who were innocent bystanders in their cases. Whether that data was stored or looked at — a violation without a search warrant — is unknown. Just like the previous case, a pattern is emerging of local law enforcement’s ability to take private and personal information absent a search warrant.
We’ve seen glimpses of how local law enforcement uses this technology, but upon a request filed through the Freedom of Information Act, the department should give information about tools it uses, right? For that, we’ll take a look at a lawsuit filed by the ACLU of Arizona against the Tucson Police Department (TPD). The lawsuit was filed in 2014 on behalf of Beau Hodai, an investigative journalist. Hodai requested information on the StingRay device used by TPD. However, due to the non-disclosure agreement TPD had with the Harris Corporation, Hodai was denied this information based on the NDA. Fast-forward to 2016 after multiple appeals, and the ACLU got what it was after. The appeals court held that when TPD failed to release records, it violated the public records laws in Arizona. This shows that while citizens are supposed to be granted access to information on technology that’s used against them, larger entities will use technicalities to fight giving that information out.
We’ve focused quite heavily on local law enforcement, so now we’ll zoom out to a larger entity. In 2016, the Department of Homeland Security (DHS) disclosed knowledge of multiple unauthorized cell site simulators in and around Washington D.C. DHS explains there isn’t much to be done, goes on to blame the phone companies for poor security, and further deflects the reason for failing to stop the malicious cell site simulators to cost and lack of equipment. As far as we know, DHS still hasn’t determined who was responsible for placing these illegal cell site simulators in D.C. — a foreign intelligence agency, corporate spies, an organized crime ring, or a rogue element of our own government. According to a 2018 article by the Electronic Frontier Foundation (EFF), “DHS doesn’t know who’s operating them or why, or whether these fake cell towers are installed elsewhere in the country.” The prior cases focused on civilians, Jane and John Doe, working hard to live the American Dream, but this one potentially violated the privacy of many high-ranking politicians (including foreign nationals) in our nation’s Capitol. The question remains: if senators and dignitaries can be spied on, how can civilians protect themselves from this technology?
What Can You Do?

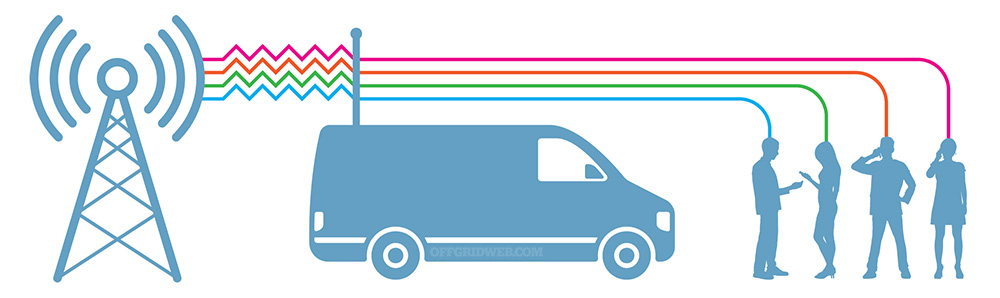
Above: The StingRay is capable of silently intercepting calls, text messages, and other data from all devices within its operational radius — that may include the target of an investigation and everyone else nearby.
Directly protecting oneself from cell site simulators is virtually impossible, since you have very little control over which cell tower your phone is using, and no way to know for sure if it’s legitimate, but there are other steps you can take. It must be remembered that the same data collected by the StingRay, and much more, is available from your cell phone provider via a warrant.
The use of Virtual Private Networks (VPN’s) to direct and encrypt your internet traffic is a basic step to start a privacy journey and is something I suggest everyone use. However, the best way to prevent a StingRay, and your cellphone provider, from gathering information on you is the proper use of two items: a burner phone and a faraday bag. The faraday bag is the most accessible and user-friendly option. Buying a reputable bag — not just an Amazon brandless bag — can make all the difference in your phone’s ability to block GPS tracking. I’ve had good experiences with Mission Darkness (mosequipment.com) bags, and SoCal Offgrid wrote about his experience with EDEC Digital Forensics’ OffGrid line of bags (offgrid.co) in Issue 48. Using it is simple; put your burner or daily-use phone in the bag and close it. The signals will be blocked, and the device cannot be communicated with. The obvious drawback to this method is that your phone also can’t send or receive calls, texts, or any other data while it’s inside the bag.
If it’s used properly, a burner phone can give you great privacy; with improper use, it can lead right back to you. Using a burner phone in the same way a daily phone is used — i.e. contacting your spouse, talking to friends and family, not using secure messaging and calling applications — gives the same information to cell phone providers (or StingRays) as a daily use phone. Collecting that data and showing the same patterns of life in two devices can easily link a person to those devices. It’s critical to be cautious about keeping your burner phone isolated from your other electronics and networks. For more details, refer to W. Dean Freeman’s article on burner phone basics in Issue 52.
Lastly, there are unconventional and old-school spycraft techniques for communication. One that’s becoming more popular to talk about, making it more common now, is the use of video game chat functions. Though it’s less obvious than communicating through a phone, most online games don’t dispose of chat logs or have end-to-end encryption, so the messages (and the user’s IP and account information) can still be revealed via search warrant. This is mostly a matter of security through obscurity, which isn’t ideal. Another technique, and one still used today, is a dead drop. Storing a flash drive or SD card in an unlikely location, such as drilled into a tree or concrete wall, allows users to create an offline file sharing system. However, this secret location is only secret when it’s not talked about. Failing to understand proper operational security, a.k.a. OPSEC, paves way for all the private information to become public, or worse, available to an adversary. It’s wise to encrypt any data you share via dead drop, so that any third party who accidentally finds it won’t be able to access it.
The Future of Cell Phone Surveillance
The StingRay is a device that has been used against citizens and criminals without a warrant, time and time again. For every high-profile incident we know about, it’s safe to assume there are dozens more that were never revealed to the public. The device takes naivety, complacency, and blind trust in the government — an entity that employs humans just like you and I, all capable of great good or evil — to gather intelligence on our whereabouts, conversations, and so much more.
The good news is that most of the cases mentioned were quite old, and due to misuse of their devices and the media backlash it generated, L3Harris Technologies stopped selling StingRay technology directly to local law enforcement at the end of 2020. Do not cheer just yet, as Nyxcell, a competitor of L3Harris, has created its own cell site simulator. The Nyxcell can perform the same surveillance as the StingRay, but also has upgraded features for the newer phones hitting the market. Jacobs Solutions, a Fortune 500 company with $14 billion in annual revenue, offers another cell site simulator device through its subsidiary KeyW Corporation. The mysteriously barren web sites of both companies offer no information about the existence of these products or their capabilities, but Nyxcell’s slogan — “When lives and security are at stake, Nyxcell solutions get results” — certainly seems ominous given the context.
I want to leave you with this: Do not be afraid of your phones. A cellphone is an amazing piece of technology that truly helps us all on various levels, from basic communication to controlling life-saving medical equipment attached to our bodies. Just be aware of the risks taken while using them and pause to consider the information you’re revealing before you hit “send.”
Related Posts

Encrypted Radios: Off Grid Comms Offers AES-256 Encryption for CiviliansOff Grid Comms offers ready-to-use encrypted radios for civilians. They're based on the P25 digital standard with AES-256 encryption.

iPhone 14 Adds Satellite SOS and Crash Detection FeaturesThis week, Apple announced some new emergency preparedness capabilities for the iPhone 14: automatic car crash detection and satellite SOS.

New: Holosun DMS Red Dot + Thermal Hybrid OpticThe new Holosun DMS-TH and DMS-NV optics feature an AEMS-style red dot with a secondary thermal or digital night vision overlay function.
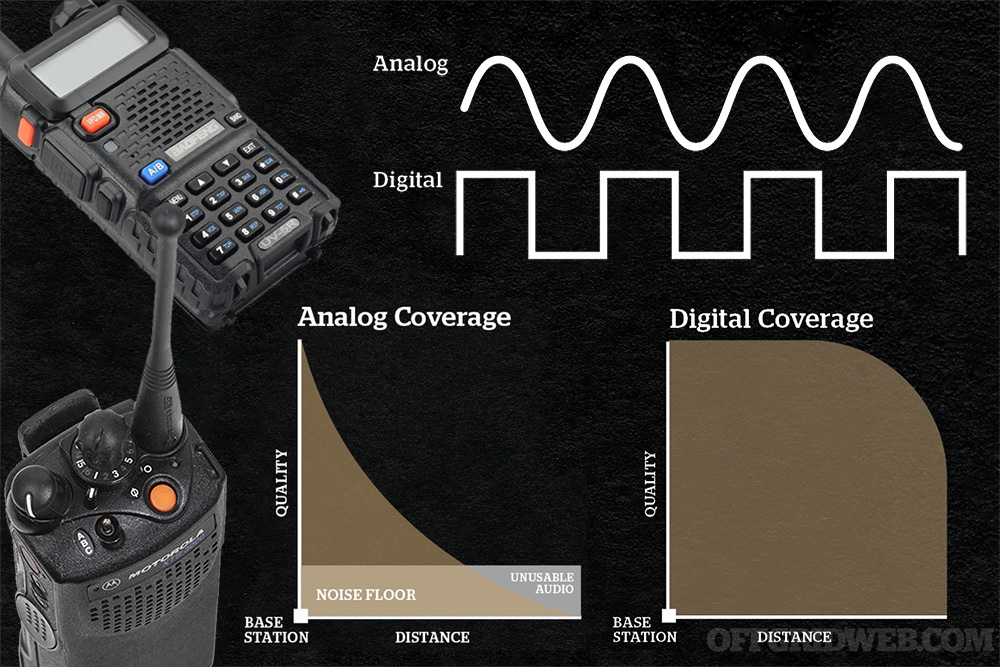
Infographic: Digital vs. Analog RadiosExplaining all the details of the digital vs. analog radio debate would require a lengthy technical article, so we'll give you the basics.

Plate Carrier Radio Setups: Safariland Liberator & Silynx ClarusHere are two plate carrier radio setups from Safariland and Silynx that integrated our encrypted handhelds into our load-bearing gear.

New: Juggernaut Case Plate Carrier Phone Mount 2.0This week, Version 2.0 of the Juggernaut Case plate carrier phone mount was unveiled with improvements to the retention and hinge design.

New: Armasight Contractor Thermal OpticsThe Armasight Contractor series includes the Contractor 320 3-12x25mm and 6-24x50mm. Both thermal optics are designed and built in the USA.

Review: Juggernaut Case Plate Carrier Phone Mount & Car ChargerI used parts from Juggernaut Case and RAM Mount to adapt my smartphone to a plate carrier and a inductive car charger in my Toyota 4Runner.

Jerry Saunders Interview: At Home in the InhospitableJerry Saunders is a Marine veteran, bladesmith, founder of Corvus Survival, and expert in cold-weather survival skills.
The post Cell Phone Surveillance: Can They Hear You Now? appeared first on RECOIL OFFGRID.
By: Offgrid Staff
Title: Cell Phone Surveillance: Can They Hear You Now?
Sourced From: www.offgridweb.com/preparation/cell-phone-surveillance-can-they-hear-you-now/
Published Date: Sun, 22 Jan 2023 12:00:27 +0000
-------------------------------------------------------------------------
Did you miss our previous article...
https://outdoorsnewswire.com/survivalist/10-celebrity-preppers-ready-for-anything
 CampingSurvivalistHuntingFishingExploringHikingPrivacy PolicyTerms And Conditions
CampingSurvivalistHuntingFishingExploringHikingPrivacy PolicyTerms And Conditions
