If you’re reading this, there’s a strong chance you own a smartphone. Most people do these days. We use them less and less for calling and more for living our digital lives: banking, commerce, social media accounts, business deals — our phones are basically an extension of ourselves. Unfortunately, we also find ourselves in an increasingly less-permissive environment, legally and socially. Governments the world over have (both legally and illegally) increased their digital surveillance capabilities at an alarming rate, as the Snowden leaks revealed to the world. NGOs and online sleuths are able to leverage Open-Source Intelligence (OSINT) to track people through cyberspace and the real world, feeding information to authorities or to cancel-culture rage mobs. Abusive partners looking to further control and isolate their spouses may also leverage their phones against them.
Spy fiction has for years popularized the concept of a “burner phone.” The entire first season of the hit HBO crime drama The Wire really revolved around Baltimore PD’s attempt to thwart a drug gang’s use of burners. But when it comes to burner phones in the real world, what are the facts? How do they work? What are the legal and technical hurdles you might find yourself facing should you choose to acquire and operate one? What tradecraft is really needed in order to make a burner phone even worth it? I’ll explore the answer to these and other questions in this article.
What is a Burner Phone?

At a minimum, a burner phone is one that we don’t care about and don’t intend to use for long. They may be used once or just a few times. The phone will often be ditched or destroyed after use, so we want one that’s inexpensive but robust enough to do what we need to do, especially if the intention is to use the internet and online applications at all.
Really, though, the value of a burner phone is in disassociating ourselves from the phone. We don’t want our name associated with the IMEI (International Mobile Equipment Identity) of the phone in any way. IMEI is a globally unique identifier for a phone. While a serial number identifies a phone in terms of its manufacturer, the IMEI is what identifies a phone on the cellular networks. It must be globally unique in order to facilitate roaming between networks. Even if you switch out SIM cards, the IMEI of the phone is still used to identify the phone.
When you sign up for a phone contract with, say, Verizon or AT&T, you’ll be asked to show ID, sign up with a credit card for billing, etc. In their database, they’ll have your phone IMEI associated with your account. This creates an extremely strong association between the two. If you travel to another country and get a local SIM card, you’ll have a new SIM Serial Number (SSN) and even a new MSISDN (Mobile Station International Subscriber Directory Number; i.e., the phone number). However, your IMEI will remain static.
Preventing an association between our identity and an IMEI, and having a phone that can be discarded to make tracking or successful Signals Intelligence (SIGINT) or Communications Intelligence (COMINT) targeting harder is what most people are thinking of when they think about a burner phone.

In another context, a burner really just focuses on the “disposable” aspect. You may still want a strong association between the device and yourself, but don’t want to risk your real phone or its data. In this context, you may also want a burner laptop as well, not just a phone. You may just re-image the devices before and after or you may just ditch them after.
Why Would You Need a Burner Phone?
The media tends to focus on the bad actors when it comes to any tool (guns, anyone?). They’ll bring up spies, terrorists, and drug dealers as reasons why telecommunications should be heavily regulated and everyone should have to have their device tied to their identity. Of course, activists who are afraid they may be targeted for political persecution, as well as just your general privacy enthusiasts would also want access to a burner phone. But there are many perfectly legal, sensible reasons to use a burner. Examples of these include:
- An engineer or executive from a technology company traveling to China, who is afraid his device may be targeted by the authorities for industrial espionage purposes.
- A tourist who is afraid of being made to unlock a device when clearing customs.
- A woman whose abusive boyfriend has access to a phone he gave her, but who needs to communicate without him finding out.
How to Buy a Burner Phone

Above: I purchased a Moto e and unlimited voice and text plus 1GB of data, in cash, at my local Target store. I didn’t need to show ID at point of sale.
At a minimum, a burner phone is a prepaid phone. Depending on the laws of your jurisdiction, and the policies of both the store you buy from and the carrier you choose, it may be more complicated. In much of the world, you’re not going to be able to buy a prepaid phone or even a SIM for your current phone without showing ID. You may not be able to buy with cash, either.
In 2010, there was an attempted car bombing in Times Square in New York City. The terrorists used “burner phones” as part of the trigger system for their device. Predictably, as in all such tragedies, politicians wanted to be seen as “doing something” and introduced legislation to eliminate “burner phones” in U.S. S3427, known as the Pre-Paid Mobile Device Identification Act. It didn’t pass, but some stores adopted the policy anyway.
So, what’s the process like today, and what considerations do you have to be aware of? For research purposes, I was able to go to my local Target and buy a Tracfone Moto e and a plan card. I didn’t have to show ID, and I was able to pay cash. I did have to ask the sales associate to unlock the phone from the shelf for me.
Honestly, it was really easy and straightforward. And depending on your threat model, that might be enough. The woman in an abusive relationship might go in and make her purchase, just as teenagers do daily. However, if “jealous boyfriend” isn’t the adversary you’re concerned with, then you’ll also want to take tradecraft into consideration.

Above: Tracfone and other prepaid mobile services require that you purchase your minutes and data separately. The phone doesn’t come with anything included in the box.
Purchase Precautions
We live in the most surveilled time period in all of human history. We’re constantly being tracked, both online and offline. We know that, which is why we want a burner. But if our goal is to completely disassociate from the phone, even under the scrutiny of knowledgeable and well-equipped state-level adversaries, we have to be craftier.

Here’s a list of things to take into consideration:
- We never want our actual phone and the burner phone to be active in the same location, or in relative proximity to each other. In fact, we don’t want our phone to have been near the store where we purchased the burner, and certainly not when we purchased it. Even if we’re not just worried about the cellular service, we don’t want any other emissions from our phone (BTLE, Wi-Fi probes, etc.) to leave a digital bread crumb trail. You might think turning your phone off is enough, but that’s not always true. For example, Apple’s iOS 15 added a new “findable after power off” option for iPhones.
- In my local Target, there are surveillance camera bubbles on the ceiling in a matrix, about 8 to 10 feet between each other. Some of those may be decoys, but it’s safe to assume you’re on camera the entire time you’re in the store. You might want to consider wearing a mask for privacy — most people will assume you’re only concerned about getting sick.
- There are speed and traffic cameras all over. Many of us also have toll transponders, or vehicles with built-in cellular Wi-Fi systems. There are plenty of opportunities for our vehicle to be tracked going to or from the store.
The obvious solution to these considerations is the use of one or more cutouts. A cutout is an individual whose role is to ensure that two other individuals (such as an intelligence officer and his or her handler) don’t have to meet together. In this case, you get a cutout to have someone else go make the purchase someplace outside of your immediate area of operations (AO), and then meet for the pickup. You either meet for the pickup in a third location, or receive the phone via dead drop (a pre-arranged location to exchange goods without meeting).
It’s also worth noting that if you don’t buy a plan card in the store with cash, you’ll need to provide credit card information when you activate the phone later.
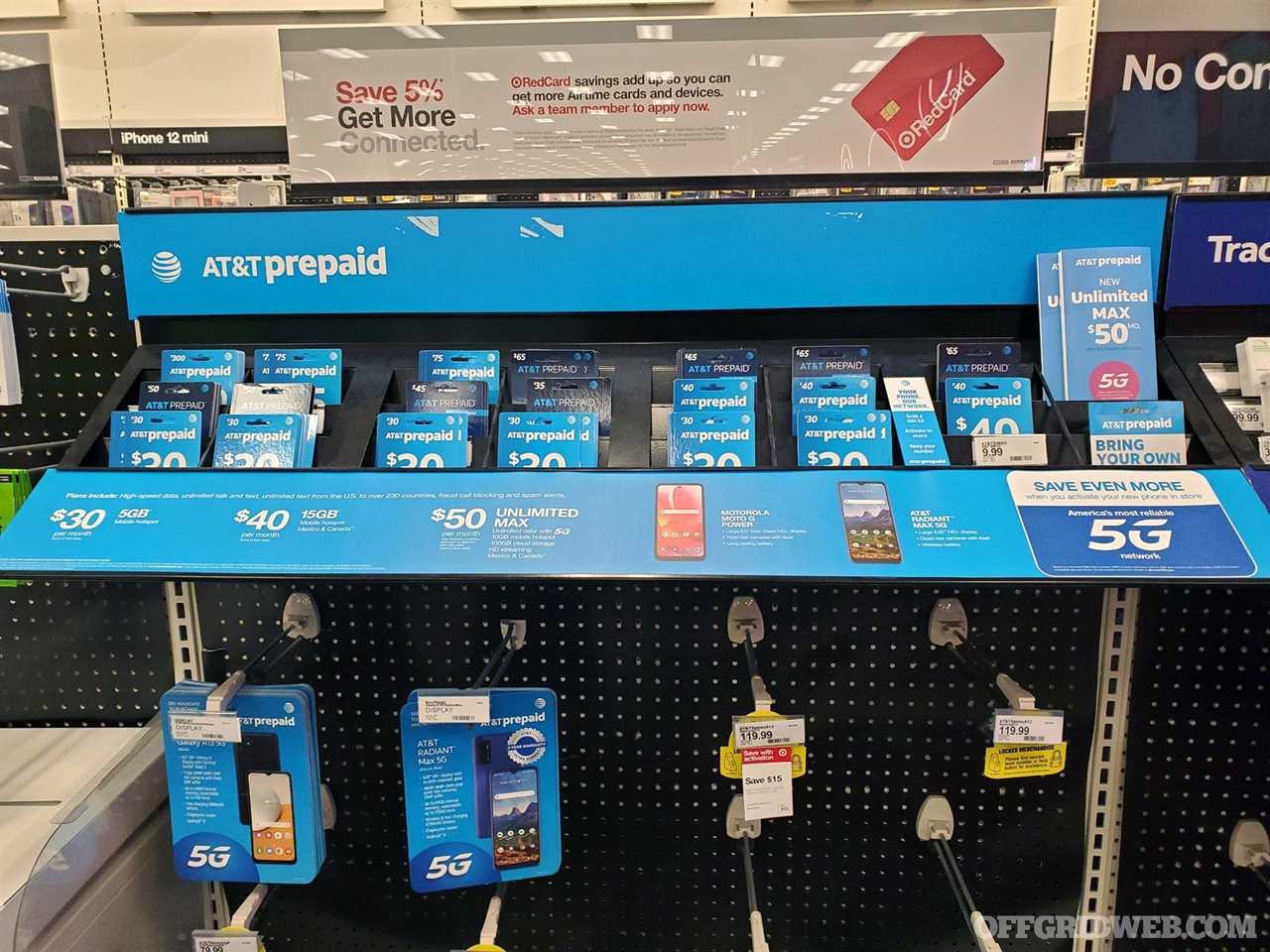
Above: Big-name carriers like AT&T have prepaid options, but may have policies and technical controls in place to limit their usefulness as “burner” phones, even though there’s currently no legislation in place in the U.S. mandating this at a federal level.
How to Set Up a Burner Phone
The process for activating the phone is going to differ depending on the carrier you choose. Some may make it more difficult than others, given our intended purposes and constraints.
The process for Tracfone is relatively straightforward:
- Turn on the phone — remember not to do this near your primary phone, home address, workplace, etc.
- If you got one of the Android models, make sure you turn off all the location sharing and other Android privacy-spoilers.
- From a computer (because the website won’t work on the Android Chrome browser, so you can’t just connect the phone to Wi-Fi), go to the Tracfone website.
- Click to activate
- Provide the PIN from your plan card
- Provide the IMEI and select a zip code you want your phone number to be from
- Create an account
- Reboot the phone
- Now it works!
How to Activate a Burner Phone
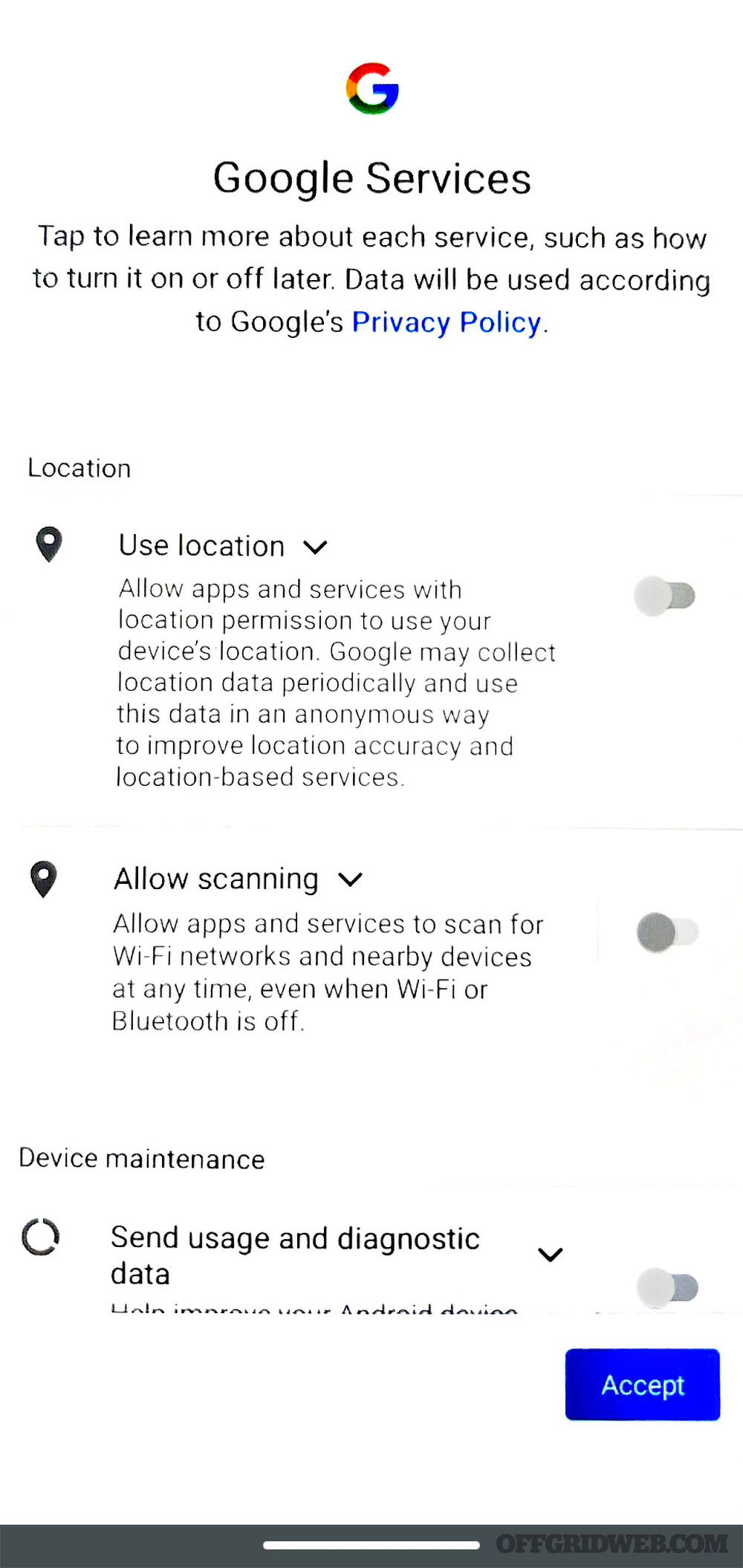
Above: Make sure to opt out of all Google tracking and diagnostic “services” when you initially power on the device.
Here are the facts, based on my experience at the time of writing this. The Tracfone activation page won’t progress past the IMEI input and zip code selection if you’re using a well-known VPN service or Tor. I wasn’t able to do it while using ProtonVPN, for instance. This is obviously in order to tie a real IP address to the activation so that an association can be attempted later.
However, when they ask for an email address, they don’t have any requirements for this email address. In fact, I was able to use temp-mail.org/en to get a temporary email address and use that. No email was sent to this address during its lifetime, and I verified that it’d receive email by sending one to myself at the randomized address.
My recommendations for activation tradecraft are:
- Activate the phone away from home, with a public computer if possible (library, cyber cafe, etc.) If doing it from a coffee shop, make sure you disable Bluetooth and any sharing, change your Wi-Fi MAC address, etc.
- Use a temporary email address to activate the accounts.
- Either get your cutout to do this for you, or be cautious of any form of evidence of your presence at this location that might come back to haunt you later. This may include CCTV footage, credit card transaction records, tracking data from your other electronic devices, or even eyewitnesses who remember your appearance.
How to Use a Burner Phone
The operational security (OPSEC) around running a burner phone is based largely on your threat model, or the map between your assets (what you have to protect), the threats against those assets, and how the threats may attempt to exploit weaknesses to attack those assets. The woman in an abusive relationship has a much different threat model than the political activist, for instance.
A complicated threat model will include:
- Attacks against your anonymity by tying you to the device (e.g. surveillance of locations where the device is commonly used).
- Attacks against your privacy by tying the device, and thus you, to specific locations at specific times (e.g. triangulation or GPS tracking).
- Attacks against the confidentiality of your communications (e.g. wiretapping).
- Attempts to determine who in your network communicates with whom and map the “social networks” you’re part of (if your burner only contacts your known associates, who aren’t using burners of their own, that’s a clue to your identity).
Making the mistake of logging into online services, especially those such as Google or Facebook, will instantly tie your phone’s IP address to your account. Your Google info can be subpoenaed, and then the carrier will be subpoenaed for information on the phone that had the IP address, thus tying you to the phone.
There have been numerous cases of phone locations being subpoenaed during an investigation. In 2020, an individual was investigated by police merely for having tracked a bike ride on Google Maps past the location of a robbery at roughly the same time. And we’re all aware of the mass leveraging of geolocating phones during the January 6 incident.
All voice calls and SMS text messages, as well as internet traffic, can be subject to lawful intercept due to the Communications Assistance for Law Enforcement Act (CALEA). The scope of the warrant can be for call identifying information (CII), such as information on who called whom and any dialed digits, or might extend to Call Content (CC), which is recordings of the actual phone call or captures of digital data exchanged. Avoid the use of unencrypted communications, even with a burner phone.
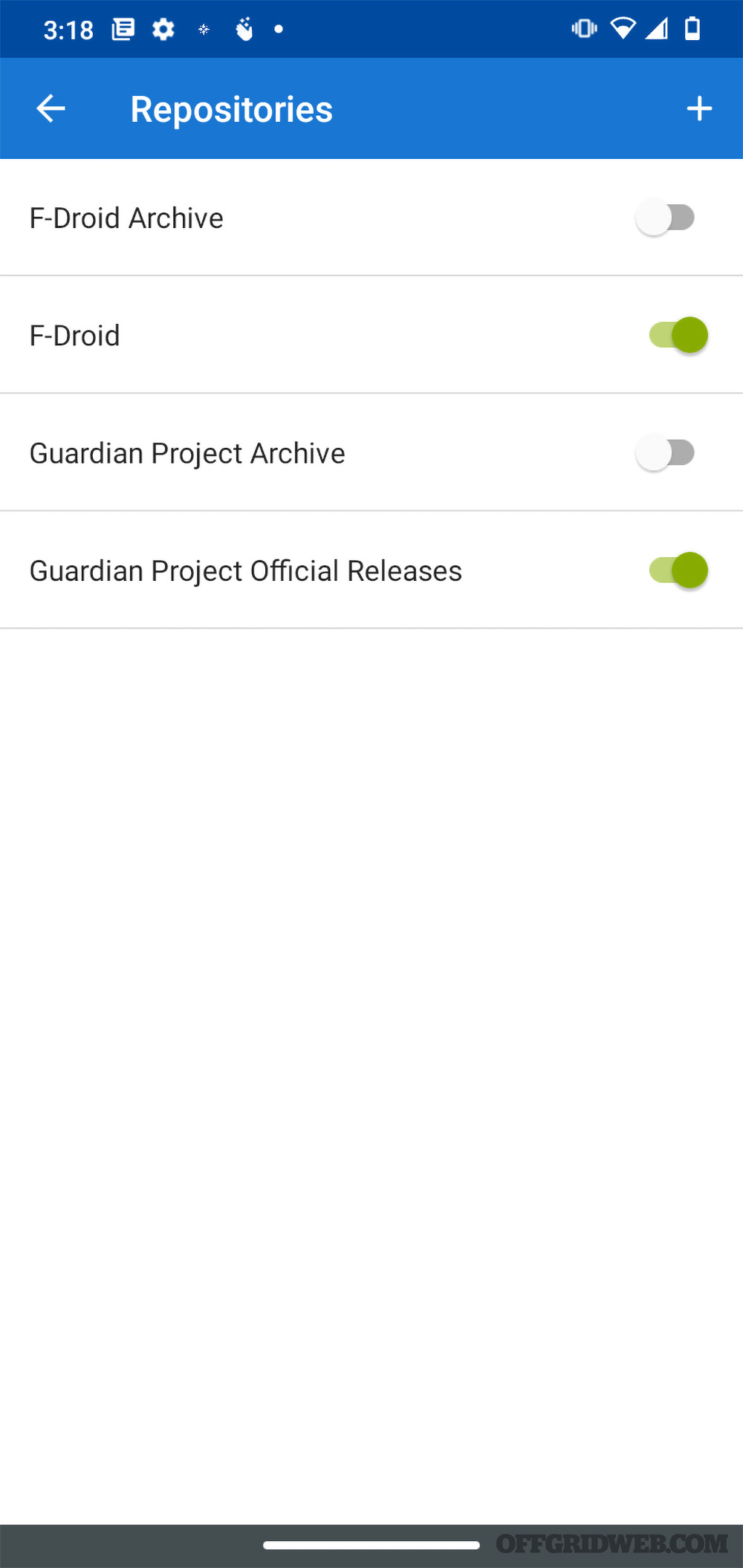
Above: F-Droid is a third-party app store that supplies open-source software. By enabling the Guardian Project repo, you can get privacy-focused applications to help bolster your anonymity and increase the value of your burner phone.
Important Privacy Tips
At a minimum, follow these tips to mitigate threats to your mobile phone and privacy:
- DO NOT log into a Google account for Android, or in a browser. This should go without saying.
- DO NOT enable any telemetry, tracking, optimization, or customization features.
- DO NOT enable biometrics (thumbprint, facial recognition, etc.). Stick with a PIN. An alphanumeric pass phrase is best. Use one that’s not shared with any of your other known accounts.
- DO NOT power up your device in or around your home, work, contracted cell phone, or anything else electronic that can be used to tie you in time and space to the burner phone conclusively.
- DO install Signal manually without using Google Play.
- DO install F-Droid to allow you to install a few extra open-source applications (OpenStreetMap, and some others discussed below).
- DO commit important phone numbers to memory and avoid saving them as contacts.
- DO set up a system of challenges/responses with your associates to establish your identity on a human level. For example, think of the classic “flash” and “thunder” sign/countersign combination Allied forces used to identify each other on D-Day. Since you have gone to great pains to undermine technological identification associations, and you may be cycling through burner phones regularly, this serves as a low-tech fail-safe to confirm you’re speaking with the right person.
Mitigating social network link analysis is more difficult. In intelligence analysis, this refers to the process of graphing subjects (typically people) via associations to each other. Subjects who have the most associations are either the most important person in the network (the “Center of Gravity,” or COG), or a courier/cutout for that individual.
Network traffic analysis, such as seeing what phone numbers call what other numbers, or what IP addresses visit other IP addresses, can be used to build those associations. Thus, avoiding direct communication with attributable endpoints, such as known phone numbers or email addresses, is important in this context.
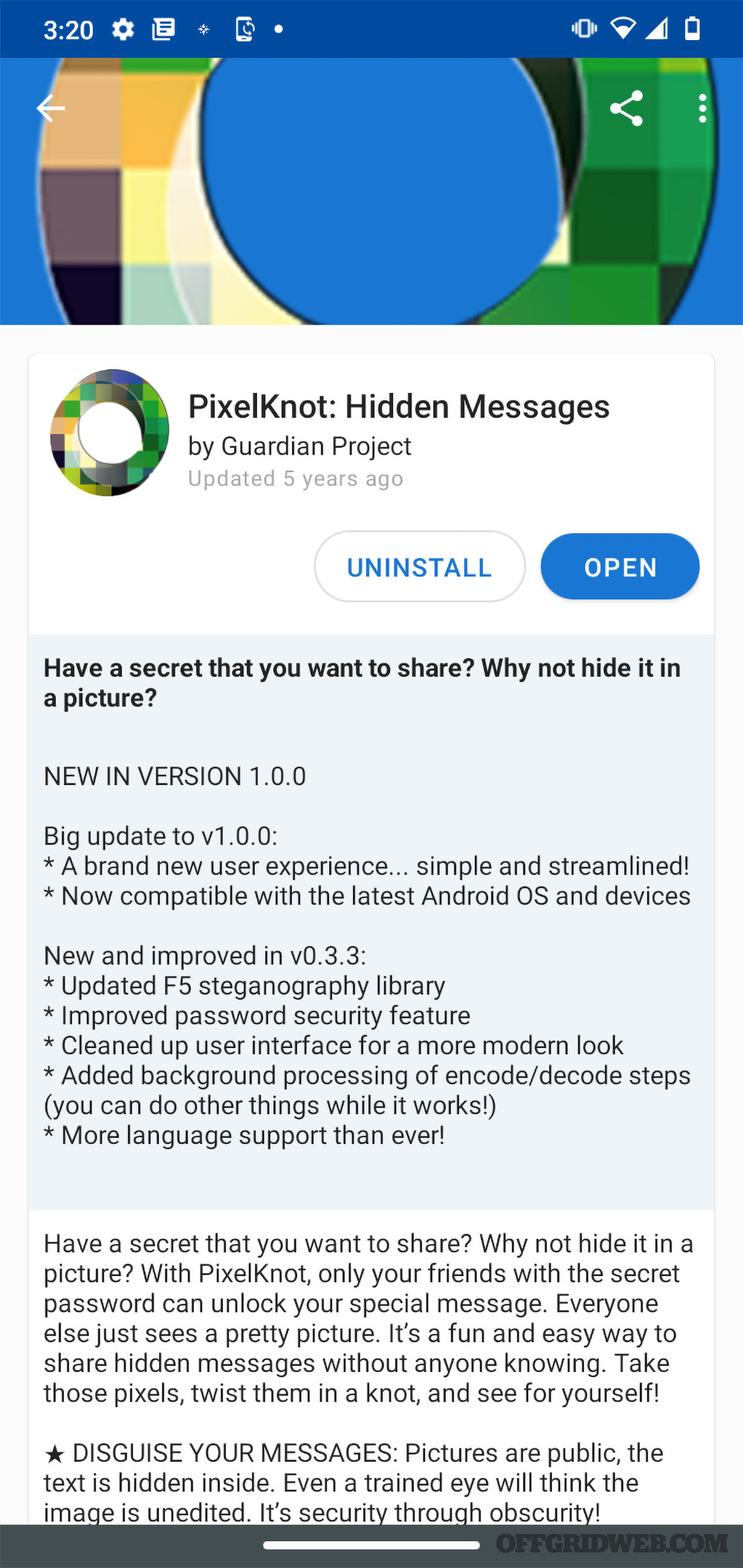
Above: PixelKnot is a digital steganography application for Android that allows you to securely embed messages in photos, which can then be distributed via anonymous bulletin boards and image-sharing sites to your compatriots.
Covert communications methods, such as steganography, can help mitigate this threat — refer to our article in RECOIL OFFGRID Issue 45 for more details on how to use digital steganography to send messages discreetly. You can gain access to a steganography app through the F-Droid app store by enabling the Guardian Project repository and then installing PixelKnot. You can install Tor browser clients via F-Droid as well.
Burning the Burner

When you’re done with your burner, you’ll want to get rid of it. How you do this will largely depend on the why. In most cases though, you’re going to want to securely dispose of the device and not just toss it into the trash can while on the run, à la Jason Bourne.
Assuming time permits:
- Perform a factory reset of the device.
- Ensure that you have physically scrubbed it of fingerprints or other biological remnants of your time with the device.
- Physically destroy the device to render it inoperable, and more to the point, to ensure that data is physically non-recoverable.
Above: Before tossing your burner phone, make sure to do a factory reset at a minimum. Wipe it (both figuratively and literally with a cloth) and physically destroy it as well, if time permits and your threat model justifies it.
FAQ
- Q: What is the point of burner phone?
A: Burner phones, or a “burner”, is an mobile phone designed for temporary, sometimes anonymous, use, after which it may be discarded.
- Q: Are burner phones legal?
A: Burner phones are legal if the use of a burner phone is for acts that are not considered illegal.
- Q: Are burner phones traceable?
A: A burner phone number can be traced, but it is difficult to trace a burner phone without specialized tools.
Conclusion
In today’s digital world, threats to privacy and security of individuals abound. Those who, for whatever reason, require anonymity can still get it through the use of prepaid cell phones. Making the jump from a mere prepaid phone to a burner requires judicious application of operational security procedures and tradecraft. These precautions will limit the opportunities for state and non-state actors to be able to tie your real-world identity to the device and then leverage the device against you by tracking you, both online and in the real world.
Read More
Don't forget to subscribe to Recoil Offgrid's free newsletter for more content like this.
- Landline Phones: Make the Right Call
- Emergency Communications
- Off-Grid and In Touch: Satellite Phones for Survival
- Cell Phone Surveillance: Can They Hear You Now?
The post Burner Phone Basics: How to Set Up an Anonymous Prepaid Phone appeared first on RECOIL OFFGRID.
By: Offgrid Staff
Title: Burner Phone Basics: How to Set Up an Anonymous Prepaid Phone
Sourced From: www.offgridweb.com/preparation/burner-phone-basics-how-to-set-up-an-anonymous-prepaid-phone/
Published Date: Tue, 14 Nov 2023 12:00:19 +0000
-------------------------------------------------------------------------
Did you miss our previous article...
https://outdoorsnewswire.com/survivalist/tasers-laws-in-utah-are-they-legal
 CampingSurvivalistHuntingFishingExploringHikingPrivacy PolicyTerms And Conditions
CampingSurvivalistHuntingFishingExploringHikingPrivacy PolicyTerms And Conditions
