Unless it's your first day on the internet, you're probably aware that downloading certain files can be a serious mistake. It doesn't take a cybersecurity expert to know that double-clicking the TotallyNotAVirus.exe file that mysteriously appeared in your downloads folder is a bad idea. If you're a bit more security conscious, you probably also know that PDF files, Excel spreadsheets, and Word documents can also contain malicious code. But how many times have you considered the possibility of malware hidden inside an image file? A sophisticated hacking group known as Worok has developed a new type of malware that can be concealed in innocuous-looking PNG images, and they've been using it to target governments and large corporations around the world.

Take a look at the soothing blue abstract image above. This is one of the actual PNG images that was used to distribute Worok's info-stealer malware payload. According to ESET's We Live Security blog, the PNG malware has been used to attack the following high-value targets:
- A telecommunications company in East Asia
- A bank in Central Asia
- A maritime industry company in Southeast Asia
- A government entity in The Middle East
- A private company in southern Africa
- An energy company in Central Asia
- A public sector entity in Southeast Asia
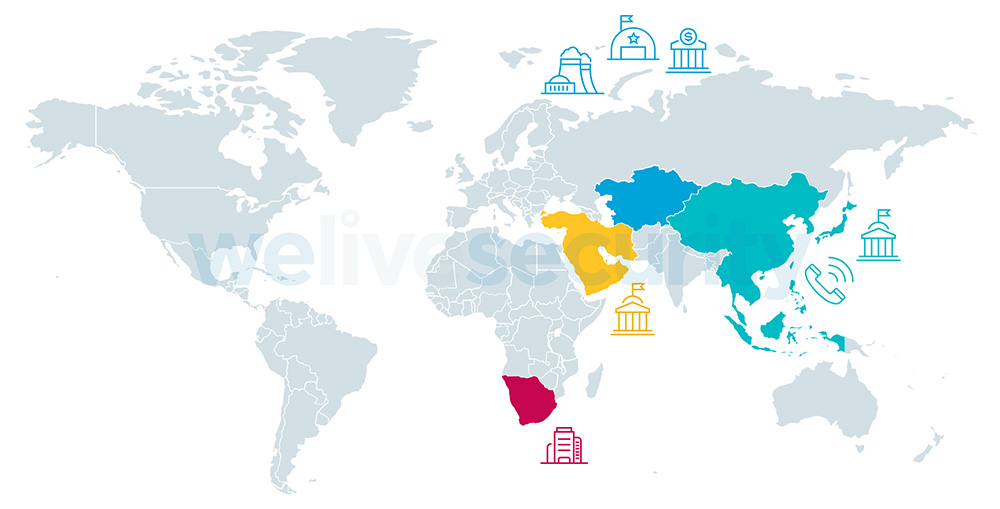
Above: This map from ESET's We Live Security offers a quick look at some of the countries where cybersecurity researchers have found Worok's malicious PNG files.
How is Malware Hidden in PNG Images?
This question gets very technical very quickly, so we'll give you the short version. If you want the full explanation, go read the We Live Security article or the Avast article.
Neither ESET nor Avast have determined the exact initial compromise point, but it's known that the infection starts when some code is executed to create a few malicious DLL files in the Windows System32 folder. Those DLLs then execute one of two malware loaders: CLRLoad or PowHeartBeat. Next, a second-stage DLL known as PNGLoad extracts the final PowerShell script payload that's hidden inside a PNG file.
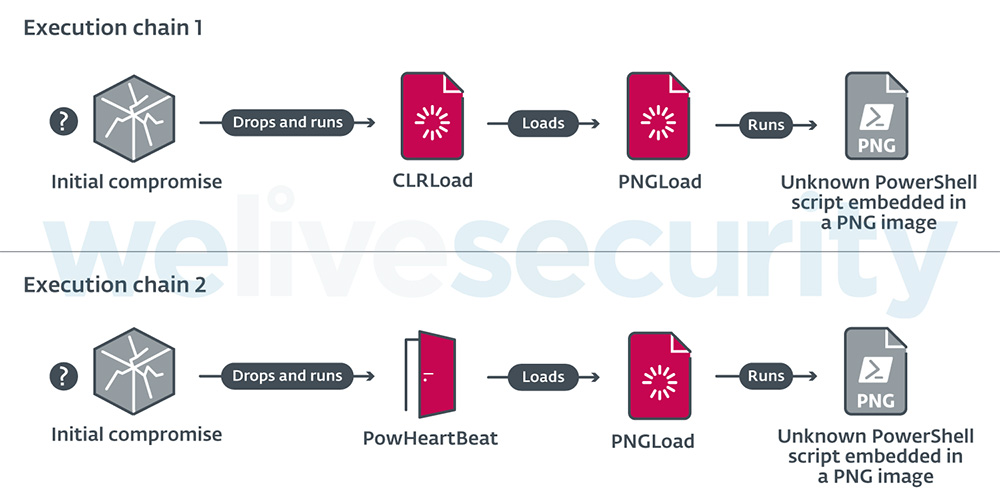
Above: A flowchart of the two known execution chains for the PNG malware. (Source: We Live Security)
Worok used a process called LSB (least significant bit) encoding which “embeds small chunks of the malicious code in the least important bits of the image's pixels,” according to BleepingComputer. This is actually a form of steganography (i.e. hiding data inside an image file), a topic we've discussed in our previous article Steganography: More than Meets the Eye.

Above: Through LSB encoding, two pixels in an image can conceal one byte of hidden data. The center image shows Worok's RGB bit planes without hidden data, and the right image shows LSB bit planes alongside a visual representation of their embedded data. (Source: Avast)
Once this complex infection process is complete, the PNG file payload installs “a custom .NET C# info-stealer” called DropBoxControl. This abuses DropBox accounts created by Worok hackers to upload or download files and execute commands remotely on the infected machine.
What Can Worok's PNG Malware Do?
According to Avast, the DropBoxControl backdoor can perform the following commands:
- cmd — Run a command prompt with parameters given by the attackers
- exe — Execute a .exe file with parameters given by the attackers
- FileUpload — Download files from the attackers' DropBox onto the victim's computer
- FileDownload — Upload (i.e. steal) files from the victim's computer
- FileDelete — Delete any file from the victim's computer
- FileRename — Rename a file from the victim's computer
- FileView — Send info on the properties (i.e. name, size, last access time) of all files inside a selected directory
- ChangeDir — Select a different directory on the victim's computer
- Info — Send computer information (including hostname, IP address, explorer.exe version, and available hard drive space) to the attackers
- Config — Update the encrypted DropBoxControl backdoor settings (a file called ieproxy.dat located in C:\Program Files\Internet Explorer)
In other words, the attackers essentially have complete remote control over the victim's computer and all of its files at this point.
Who is Worok?

Above: Much like the destructive ransomware known as Petya, some have speculated that Worok's malicious PNG files are a state-sponsored form of cyber-warfare.
Cybersecurity experts don't know exactly who is behind these attacks. However, based on the high-profile nature of the targets, the espionage-oriented functions of the malware, and the sophistication of its delivery method, it appears likely that Worok is a state-level (or state-sponsored) hacking group. According to Avast, “one of the DropBoxControl connections was monitored from an IP associated with the Ministry of Economic Development of Russia.”
Avast also noted that the authors of CLRLoad and PNGLoad are likely a different, more experienced entity than the authors of the final stage, DropBoxControl. They noted that “the code quality [of DropBoxControl] is debatable at best,” explaining that it “contains a lot of redundant code” and even saying it “looks like a school project.”
You're unlikely to encounter one of Worok's malicious PNG files unless you work for a government entity or Fortune 500 company, but it's still worth remembering that even ordinary-looking image files can contain malware. Download with care.
Related Posts

Burner Phone Basics: How to Set Up an Anonymous Prepaid PhoneToday, threats to privacy abound. Those of us who require anonymity can still get it through the use of a prepaid, disposable burner phone.

iPhone 14 Adds Satellite SOS and Crash Detection FeaturesThis week, Apple announced some new emergency preparedness capabilities for the iPhone 14: automatic car crash detection and satellite SOS.

New: Bushnell BackTrack Mini GPS UnitThe new Bushnell BackTrack Mini GPS unit offers navigation, weather tracking, and Bluetooth connectivity at an affordable price point.
A Quick Look at Smartphone Security AppsWe looked at a few smartphone security applications that can help you protect yourself, your data, and your hard-earned currency.

What If You Met Someone Dangerous on an Online Dating Site?In the world of online dating, you have to make safety your number-one priority. People with honest intentions will respect that.

Bag Drop: 5.11 Tactical RUSH72 Search and Rescue PackI keep this RUSH72 backpack inside a vehicle, except for the rare occasion I’m out in the field and away from basecamp overnight.

The Knowledge Pantry: A DIY Survival EncyclopediaThe Knowledge Pantry is an offline digital stockpile of a huge variety of useful information for emergencies and survival situations.

Letter from the Editor: Glitches in the MatrixToday, we live under an ever-increasing burden of technology. It seems as if, everywhere we turn, it plays a greater role in our daily lives.

The Unfriendly Skies: Chinese Combat Drones in the Libyan Civil WarBANG — the money shot. Right in the living room. Sprayed by plaster and coughing up dust, the soldiers finally decide we should leave.
The post Worok: Powerful Malware Hidden in PNG Images appeared first on RECOIL OFFGRID.
By: Patrick McCarthy
Title: Worok: Powerful Malware Hidden in PNG Images
Sourced From: www.offgridweb.com/preparation/worok-powerful-malware-hidden-in-png-images/
Published Date: Sat, 19 Nov 2022 01:20:40 +0000
-------------------------------------------------------------------------
Did you miss our previous article...
https://outdoorsnewswire.com/survivalist/north-carolinas-pepper-spray-laws-an-overview
 CampingSurvivalistHuntingFishingExploringHikingPrivacy PolicyTerms And Conditions
CampingSurvivalistHuntingFishingExploringHikingPrivacy PolicyTerms And Conditions
